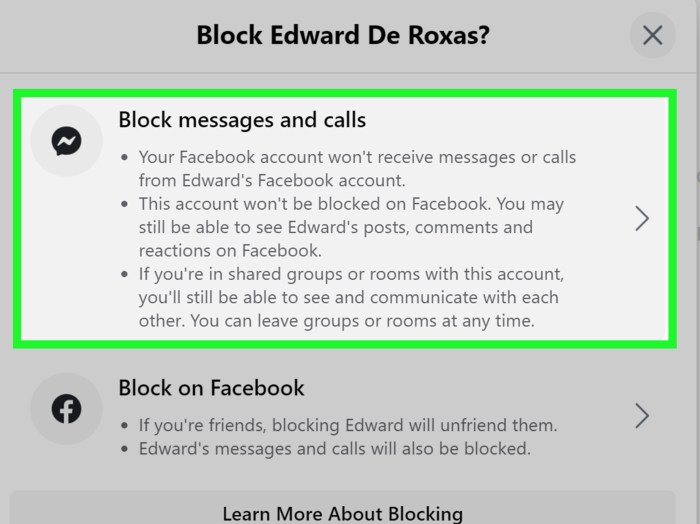
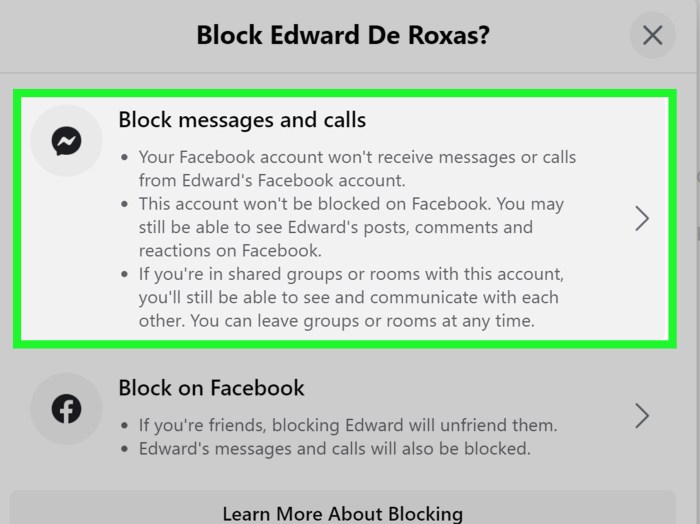
Hide Contacts on Android sets the stage for exploring the nuances of digital privacy. This guide delves into various methods for concealing your contacts, from built-in Android features to third-party apps. We’ll cover the security implications, technical aspects, user experience, and compatibility across different Android versions. Ultimately, we’ll empower you with the knowledge to safeguard your contact information effectively.
Understanding how to hide contacts on Android devices is crucial in today’s digital landscape. Privacy is paramount, and this comprehensive guide equips you with the knowledge and tools to manage your contact data with confidence. We’ll examine different approaches, analyze their strengths and weaknesses, and provide insights into the security implications of each method.
Understanding Contact Hiding Methods: Hide Contacts On Android
Protecting your personal information is crucial in today’s digital landscape. Knowing how to effectively hide contacts on your Android device can enhance your privacy and security. This guide explores various methods for concealing contacts, outlining their advantages and disadvantages, and comparing their effectiveness in providing privacy.Contact privacy is a multifaceted concern. Different methods offer varying degrees of control and discretion.
Understanding these options empowers users to choose the approach best suited to their individual needs and security preferences.
Contact Hiding Methods on Android
Various approaches exist to hide contacts on Android devices. These methods range from simple, built-in features to more complex, app-based solutions. Understanding the different strategies allows users to choose the method that best fits their privacy needs.
- Built-in Android Features: Android offers built-in mechanisms to manage contact visibility. One common method involves creating a separate contact group and designating specific contacts to that group. These contacts can then be filtered or hidden from general view. This approach is often straightforward and integrated directly into the default contact application.
- Dedicated Contact Privacy Apps: Several third-party apps specifically focus on contact privacy. These apps often offer advanced features, such as encrypting contacts, setting custom visibility rules, or integrating with other privacy-focused tools. Examples include apps that enable users to categorize and filter contacts based on specific criteria or use encryption to secure contact information.
- Contact Management Tools: Some contact management tools allow for advanced organization and filtering. These tools might enable users to create contact groups with specific access restrictions, effectively hiding contacts from certain views or applications. These tools usually provide greater control over contact visibility than standard Android settings.
- Using Virtual Private Networks (VPNs): While not directly hiding contacts, VPNs can mask your device’s IP address, potentially improving your privacy when interacting with contacts or sharing data. This method is more focused on overall network privacy rather than direct contact hiding. This is not a direct contact hiding method but can contribute to a broader security framework.
Comparison of Contact Hiding Methods
The following table summarizes the pros and cons of each method.
| Method | Pros | Cons |
|---|---|---|
| Built-in Android Features | Easy to use, readily available, integrated with standard contacts. | Limited customization options, may not offer advanced privacy features. |
| Dedicated Contact Privacy Apps | Advanced features, greater control over contact visibility, potentially more secure. | Requires downloading and managing additional apps, potentially more complex to use. |
| Contact Management Tools | Provides advanced organization and filtering capabilities, potentially more secure than basic Android features. | May not focus solely on contact privacy, might require a separate subscription or payment. |
| VPNs | Enhances overall network privacy, potentially useful for sensitive contact interactions. | Does not directly hide contacts, requires understanding of VPN usage. |
Levels of Contact Privacy Offered
The table below demonstrates the varying levels of privacy protection offered by each method.
| Method | Privacy Level | Explanation |
|---|---|---|
| Built-in Android Features | Moderate | Provides basic control over contact visibility within the default contact app. |
| Dedicated Contact Privacy Apps | High | Offers advanced customization and potentially stronger security measures. |
| Contact Management Tools | High | Provides comprehensive organization and filtering options, often integrated with other privacy tools. |
| VPNs | Moderate (Indirect) | Focuses on network privacy, which indirectly enhances the privacy of sensitive contact interactions. |
Security Implications of Hiding Contacts
Hiding contacts, while seemingly a privacy measure, introduces several security vulnerabilities. It’s crucial to understand these implications before implementing such practices, as the benefits may not outweigh the risks. Careful consideration of potential issues like data recovery and access limitations is paramount.Hiding contacts, while providing a degree of privacy, can significantly impact data security and recovery. This can be particularly problematic in situations requiring access to contact information, such as emergencies or legal proceedings.
Understanding the trade-offs is essential for informed decision-making.
Security Considerations When Hiding Contacts
Hiding contact information can hinder data recovery efforts. Without readily available contact lists, retrieving crucial data becomes more challenging and time-consuming. This is particularly problematic in situations where immediate access to contact details is critical. For example, if a phone is lost or stolen, retrieving important contacts may be significantly delayed or impossible without alternative recovery methods.
Potential Risks Associated with Hiding Contact Information
Hiding contacts can create significant security risks. If a hidden contact is a crucial point of contact for a service or support, users may face difficulties accessing essential information or services. This is particularly problematic in emergency situations.
Impact on Data Security and Privacy
Hiding contacts, while increasing privacy, can also compromise data security. By removing contact information from readily accessible locations, individuals may inadvertently create blind spots in their security strategy. This may lead to increased vulnerability if an individual’s data is compromised in other ways. For example, if a social media account or email account linked to the hidden contacts is breached, the hidden contacts may still be vulnerable.
Ever wanted to hide contacts on your Android? It’s a simple privacy setting, but sometimes a little digging is required. It’s all about controlling who sees what, kind of like the concept of “the dungeness of mirrors” the dungeness of mirrors , where hidden reflections and hidden truths are presented. Ultimately, hiding contacts is a personal choice, a way to maintain control over your digital space.
Implications for Data Recovery and Access
Restricting access to contact information through hiding methods can significantly impede data recovery efforts. If a user needs to retrieve hidden contacts for an important task or legal proceeding, this process can be significantly delayed or even impossible. For example, if a user needs to provide contact information to a court or agency, retrieval of hidden contacts might prove difficult.
Comparison Table of Security Implications of Hiding Contact Methods
| Hiding Method | Data Recovery Impact | Security Risks | Privacy Benefits |
|---|---|---|---|
| Deleting Contacts | Difficult to recover deleted contacts; permanently lost. | Increases risk of losing crucial contacts in case of device loss or theft. | High level of privacy. |
| Using a Separate Contact App | May be challenging to retrieve contacts if the app malfunctions or is lost. | Requires maintaining multiple contact lists, potentially increasing the risk of errors or omissions. | Increased privacy, but also increases complexity. |
| Using a Hidden Contact List | Requires knowledge of the hiding method to retrieve the contacts. | Vulnerable to attacks if the method is compromised. | High privacy if the method is secure and the user is aware of its limitations. |
Technical Aspects of Contact Hiding
Android’s contact hiding mechanisms leverage a combination of software engineering principles and operating system features to effectively mask entries. The underlying technical approach often involves modifying the presentation of data without fundamentally altering the database or permanently deleting information. This nuanced method allows users to maintain the contact’s existence while restricting their visibility.The core of contact hiding is intricately linked to Android’s architecture, which is crucial for understanding the process.
Different components play specific roles in achieving the desired outcome. The intricate dance between these components orchestrates the user’s experience of a hidden contact.
Android Components in Contact Hiding
Contact hiding relies on several Android components working in concert. The Android operating system provides the framework, while applications implement the logic for displaying and managing contacts. The interplay between these components is essential for the effective management of contact visibility.
- Content Providers: Content providers act as intermediaries between applications and the underlying data. They handle the storage and retrieval of contact information. For contact hiding, these providers are crucial because they control the access to contact data and can filter or modify the results returned to an application.
- Applications: Applications, such as contact apps, are responsible for presenting the contact list to the user. Custom applications often incorporate their own logic for hiding contacts, using the content provider interface to retrieve and display data. This customization is vital for tailored user experiences.
- Activity Lifecycle: The activity lifecycle governs how contact lists are displayed and managed. Activities are responsible for showing or hiding contact information based on user interaction and application logic. The lifecycle determines when data is loaded, modified, and presented to the user.
Contact Data Management
Managing contact data involves sophisticated algorithms and data structures to effectively organize and retrieve information. This organization ensures that hiding contacts doesn’t disrupt the overall system’s performance.
- Database Queries: Specific queries are formulated to retrieve contact data, enabling the application to filter the displayed list. These queries might use selection criteria or indexes to pinpoint hidden contacts.
- Data Structures: The underlying data structures in the Android database, such as tables and indexes, play a crucial role in efficient data retrieval. Algorithms for indexing and searching can significantly impact performance, particularly when handling large contact lists.
- Filtering Algorithms: Algorithms are used to filter the contact list, determining which entries are visible and which are hidden. These algorithms are often based on criteria set by the user, such as a specific name or group association.
Android API for Contacts
The Android API provides a robust set of tools for interacting with contact data. Developers utilize these tools to integrate with the underlying contact system.
- ContactsContract: This core API provides classes and methods for accessing and manipulating contact data. Developers use this API to query, update, and delete contact information, allowing the implementation of various contact management functionalities, including hiding.
Data Flow Diagram
The following diagram illustrates the data flow when hiding a contact:
(Diagram Description): The diagram depicts a user interacting with a contact app. The user initiates the hiding action. The app, using the ContactsContract API, interacts with the Content Provider. The Content Provider filters the contact data, excluding the hidden contact from the query results. The filtered data is then returned to the app, which displays the updated contact list to the user, effectively hiding the targeted contact.
Ever wanted to keep certain contacts hidden on your Android phone? It’s a pretty straightforward process, but if you’re looking for a deeper dive into customizing your privacy settings, you might also appreciate some of the innovative music projects out there, like this new compilation album by Shearwater, St. Vincent, Coldplay, and others, featuring covers of various songs, including a cool rendition of Xiu Xiu.
shearwater do st vincent coldplay on covers lp listen to their xiu xiu cover It’s definitely worth a listen if you’re into that kind of thing. Luckily, hiding contacts on Android is pretty simple to do. Just check your phone’s settings for the appropriate options.
User Interface and Experience

Crafting a user-friendly interface for hiding contacts is crucial for a seamless and intuitive experience. A well-designed UI should guide users effortlessly through the process, minimizing confusion and maximizing privacy. This involves understanding user needs, anticipating potential pain points, and providing clear and concise visual cues. The design must be adaptable to different screen sizes and operating systems for consistent usability across various Android devices.
Contact Hiding Interface Design
A successful contact hiding interface needs to be intuitive and visually appealing. Users should be able to easily identify and select contacts to hide, with clear visual indicators of hidden status. A straightforward navigation structure is paramount, allowing users to quickly access and manage their contact privacy settings.
Best Practices for Contact Hiding Interfaces
Implementing best practices for contact hiding interfaces enhances user experience and fosters trust. Clear visual cues for hidden contacts, such as a subtle icon or a different color, aid in quick identification. The use of a dedicated section for contact privacy settings, easily accessible from the main menu, streamlines the process. Providing detailed help or tutorial options, particularly for new users, minimizes confusion and frustration.
Different UI Designs for Contact Privacy Settings
Various UI designs can be employed to manage contact privacy settings. A simple list view, where users can toggle a switch next to each contact, provides a straightforward approach. Alternatively, a card-based interface, presenting each contact with a concise profile, allows users to review contact details before hiding. A hierarchical view, grouping contacts by categories or accounts, enables users to target specific contact groups for privacy management.
The chosen design should be consistent with the overall app aesthetic and user expectations.
User Experience During Contact Hiding
The user experience during the contact hiding process should be seamless and straightforward. A confirmation step, ensuring the user understands the action, is vital. Providing real-time feedback, such as a visual confirmation or a brief notification, keeps the user informed. The hiding process should be fast and efficient, preventing unnecessary delays. Minimizing the number of steps needed to hide contacts is key to maintaining a positive user experience.
UI Elements for Contact Hiding Features
This table Artikels various UI elements utilized for contact hiding features:
| UI Element | Description | Example |
|---|---|---|
| Contact List | Displays a list of contacts, potentially grouped for organization. | A list of names, potentially with a visual indicator (e.g., greyed out) for hidden contacts. |
| Switch/Toggle | Allows users to easily toggle the hidden status of a contact. | A switch next to each contact name to hide/unhide. |
| Confirmation Dialog | Confirms the action to hide the contact. | A dialog box asking “Are you sure you want to hide this contact?”. |
| Feedback Indicators | Provides visual confirmation of the action. | A checkmark or a brief animation confirming the hide action. |
| Help/Tutorial | Provides assistance for new users. | A link or icon to a help section, or a tutorial on hiding contacts. |
Compatibility and Limitations
Contact hiding methods on Android face significant compatibility challenges across various Android versions and device models. Different implementations of the operating system, varying hardware capabilities, and the constant evolution of security protocols all contribute to these limitations. Understanding these nuances is crucial for developers and users alike to ensure the effectiveness and reliability of contact hiding solutions.
Compatibility Across Android Versions
Android versions significantly impact the feasibility and effectiveness of contact hiding methods. Older versions might not support the same level of sophistication as newer ones. For example, methods relying on custom permissions or advanced encryption might not function as intended on older platforms. Compatibility issues could arise due to changes in the Android operating system’s core functionality regarding contact management.
Ever wanted to keep certain Android contacts hidden? It’s surprisingly easy to manage your privacy. While you’re exploring these options, you might also want to check out the latest Strokes track, “One Way Trigger,” a fantastic new song. listen the strokes new song one way trigger It’s a great tune, but don’t let it distract you from securing your Android contacts! Thankfully, hiding them is a simple process, allowing you to control who sees your information.
Limitations of Contact Hiding Solutions
Various contact hiding solutions exhibit inherent limitations. These limitations can range from the inability to hide contacts from certain apps (like messaging apps) to restrictions on the extent of hiding (e.g., only hiding from the contacts app but not from the phone dialer). The granularity of control over which applications can access hidden contacts can vary greatly, influencing the effectiveness of the hiding method.
Impact of Android Versions on Contact Hiding Methods
Different Android versions affect contact hiding methods in numerous ways. Older Android versions might lack the necessary APIs for implementing sophisticated hiding features, while newer versions might introduce new security features that could potentially interfere with existing contact hiding methods. The impact can vary greatly, depending on the specific hiding method employed.
Specific Requirements of Android Devices for Implementing Contact Hiding
The processing power and memory capacity of different Android devices play a crucial role in the success of contact hiding solutions. Resource-intensive hiding methods might not function smoothly on devices with limited processing power or memory. Implementing contact hiding solutions needs to take into account these device-specific limitations.
Compatibility Table
| Android Version | Contact Hiding Method Compatibility | Limitations/Issues |
|---|---|---|
| Android 4.4 (KitKat) | Limited support for advanced hiding methods. Primarily relies on app-specific solutions. | Potential conflicts with system apps, limited control over app access. |
| Android 5.0 (Lollipop) | Improved support for some advanced hiding methods. Some methods might encounter minor compatibility issues. | Potential for issues with certain third-party apps. |
| Android 6.0 (Marshmallow) | Increased compatibility for many hiding methods. Introduces changes in permissions, impacting app interactions. | Potential for hidden contacts to be visible in specific apps. |
| Android 7.0 (Nougat) | Improved security features can affect hiding methods. Potential issues with hidden contacts showing up in certain contexts. | Increased focus on user privacy. |
| Android 8.0 (Oreo) | Further advancements in security and privacy. Contact hiding might require stricter permissions. | Potential conflicts with security features. |
| Android 9.0 (Pie) and above | Enhanced security features might influence hiding methods. Stricter access controls for apps. | Potential for hiding methods to be bypassed in certain situations. |
Third-Party Apps for Contact Hiding
Beyond the built-in Android options, numerous third-party apps offer more sophisticated and customizable contact hiding solutions. These applications often provide additional features and a broader range of privacy controls. Choosing the right app depends on specific needs and priorities.
Popular Contact Hiding Apps
Several popular apps cater to contact privacy on Android. They vary in their approaches, features, and user interfaces. Understanding the strengths and weaknesses of each can lead to a more informed decision.
Comparative Analysis of Contact Hiding Apps
This section presents a comparative analysis of key features across popular third-party contact hiding apps. The comparison highlights the diversity in functionalities and the varying degrees of customization.
| App Name | Key Features | Pros | Cons |
|---|---|---|---|
| Privacy Locker | Contact hiding, app locking, file encryption, secure messaging | Comprehensive security features, robust encryption | Steeper learning curve, potential for complex configurations |
| Secure Folder | Dedicated secure folder for sensitive files, contacts, and photos | Built-in Android security, seamless integration | Limited to Android devices, less customization compared to Privacy Locker |
| Hide My Contacts | Simple interface, effective contact hiding | Easy to use, straightforward functionality | Fewer advanced features, might not suit all privacy needs |
| Secure Vault | Password-protected vault for sensitive data, including contacts | Focus on security and privacy, strong encryption | Might be less user-friendly than Privacy Locker for beginners |
Key Features of Contact Privacy Focused Apps, Hide Contacts on Android
These apps prioritize contact privacy through various mechanisms. Some employ advanced encryption, while others focus on intuitive user interfaces for ease of use. The crucial features often include the ability to conceal contacts from general view, to apply specific access restrictions, and potentially integrate with other privacy-enhancing tools.
- Encryption: Strong encryption protocols protect sensitive data, making it harder for unauthorized access.
- Customizable Hiding: Allowing users to selectively hide contacts based on specific criteria (e.g., groups, individuals) enhances control and granularity.
- Secure Storage: Dedicated storage locations within the app, or secure folders, prevent accidental disclosure of hidden contacts.
- Password Protection: Protecting access to hidden contacts with passwords or biometric authentication further strengthens security.
- Integration with other privacy tools: Some apps integrate with other privacy tools, expanding the user’s security capabilities.
Reputable Third-Party Apps for Hiding Contacts
Choosing a reputable app is crucial for maintaining contact privacy. Researching user reviews and verifying the app’s security measures can help ensure that your data remains protected. Reliable app stores and independent security reviews provide valuable information for informed decisions.
- Privacy Locker: A comprehensive app offering various privacy features beyond just contact hiding.
- Secure Folder: Built-in Android solution for secure storage of personal data, including contacts.
- Hide My Contacts: Simple and straightforward solution for basic contact privacy needs.
- Secure Vault: A vault-like app for storing sensitive data, including hidden contacts.
Privacy Settings and Permissions

Android’s built-in privacy settings offer a degree of control over personal information, including contacts. Understanding these settings is crucial when considering contact hiding apps. They often rely on or interact with these core privacy controls. Moreover, the permissions these apps request are critical to evaluating their potential impact on user data.The permissions granted to apps directly affect how they access and manage your contact data.
Careful consideration of these permissions is paramount when installing any application, especially those dealing with sensitive information like your contacts. This section delves into the relationship between Android’s privacy settings, permissions for contact hiding apps, and the importance of reviewing them before installation.
Android’s Built-in Privacy Settings
Android’s built-in privacy settings offer granular control over how apps access and utilize personal information, including contact lists. Users can manage these settings through the device’s settings menu, allowing for a degree of control over which apps can access and modify contacts. This granular control is vital for users to manage their privacy.
Permissions Required for Contact Hiding Apps
Contact hiding apps require specific permissions to function. These permissions dictate the level of access the app has to your contacts. The need for specific permissions is often linked to the desired functionality of the app. This is a crucial consideration for users to understand.
Examples of Contact Management Permissions
Apps requesting permissions for contact management vary in scope. Some common examples include:
- READ_CONTACTS: This permission allows the app to read your contact information, including names, numbers, and other details. This is a fundamental permission for apps that need to display or access contact data.
- WRITE_CONTACTS: This permission allows the app to modify your contact information. This permission is needed for apps that allow you to edit or update contact details within the app’s interface.
- DELETE_CONTACTS: This permission allows the app to delete contacts. This is a critical permission for apps that offer the ability to remove contacts, so users must be aware of this permission before granting it.
- GET_ACCOUNTS: This permission enables the app to access account information, which could potentially be linked to contact data. This permission is sometimes requested to allow seamless integration with other accounts, so users should be aware of the scope of this permission.
Importance of Reviewing Permissions Before Installation
Thorough review of permissions before installing any app, especially those related to contact management, is crucial. Misunderstanding or overlooking these permissions can lead to data breaches, unauthorized access to personal information, or other privacy violations. Understanding the potential risks and benefits is paramount for users.
Table of Permissions Required by Different Contact Hiding Apps
This table provides a generalized overview of the common permissions required by different contact hiding apps. Note that specific permissions may vary between apps.
| App Category | Typical Permissions |
|---|---|
| Contact Hiding Apps | READ_CONTACTS, WRITE_CONTACTS, potentially DELETE_CONTACTS, GET_ACCOUNTS |
| Contact Management Apps | READ_CONTACTS, WRITE_CONTACTS, DELETE_CONTACTS |
| Social Media Apps | READ_CONTACTS, WRITE_CONTACTS, potentially GET_ACCOUNTS (for account linking) |
Data Security Best Practices
Protecting your contact information, especially when using contact hiding methods, is paramount. This involves understanding the inherent risks and implementing robust security measures. By diligently following best practices, users can significantly reduce the likelihood of unauthorized access and maintain the privacy of their personal data.Ensuring data security when hiding contacts requires a multi-faceted approach, encompassing both proactive measures and reactive responses to potential threats.
This includes careful selection of tools, understanding the limitations of different methods, and adhering to strict security protocols.
Contact Information Protection
Protecting your contact list requires a comprehensive approach. First, ensure your device’s operating system and any associated apps are up-to-date. Regular software updates often include critical security patches that address vulnerabilities. Furthermore, use strong, unique passwords for all accounts, including those associated with your contact hiding app.
- Employ strong passwords:
- Use a password manager to generate and store complex passwords securely.
- Enable two-factor authentication (2FA) wherever possible.
- Regularly review and update your passwords to prevent compromise.
Implementing these measures significantly enhances the overall security posture of your device and associated data.
Security Measures for Third-Party Apps
When choosing a third-party contact hiding app, rigorous vetting is essential. Look for apps with a strong reputation for security and data privacy. Thoroughly review the app’s privacy policy to understand how your contact information will be handled. A clear and concise policy detailing data collection and usage practices is a strong indicator of the app’s commitment to your privacy.
- Verify the app’s security certifications:
- Look for certifications from reputable organizations that attest to the app’s security standards.
- Avoid apps with vague or overly broad privacy policies.
- Read user reviews and forums to understand community experiences with the app’s security.
These steps allow users to assess the app’s trustworthiness and mitigate the risk of data breaches.
Avoiding Data Breaches
Proactive measures can mitigate the risk of data breaches when managing contact privacy. Regularly backing up your device and data is crucial. In case of a breach or device loss, having a backup allows for data recovery.
- Monitor your accounts:
- Actively monitor your accounts for any suspicious activity.
- Implement multi-factor authentication wherever possible.
- Keep your software updated.
These practices can help users remain vigilant against potential threats and respond effectively to any security incidents.
Detailed Guide for Protecting Contact Information
A comprehensive guide to protecting contact information encompasses several key elements. It begins with choosing a secure device and establishing strong passwords. It then emphasizes the importance of vetting third-party apps and using them responsibly. Furthermore, the guide highlights the necessity of regular backups and active account monitoring.
| Action | Description |
|---|---|
| Strong Passwords | Use unique and complex passwords for all accounts, including those related to contact hiding apps. |
| Regular Backups | Back up your device and data frequently to enable data recovery in case of loss or breach. |
| Account Monitoring | Actively monitor your accounts for suspicious activity. |
| App Vetting | Thoroughly research and vet third-party apps before using them for contact hiding. |
This detailed guide provides a structured approach to safeguarding contact information and reducing the risk of unauthorized access.
Conclusion
In conclusion, hiding contacts on Android is a multifaceted process involving various methods, each with its own security considerations and user experience. We’ve explored the technical aspects, security implications, and user interface elements, equipping you with the knowledge to choose the most suitable method for your needs. Remember to prioritize security best practices, regardless of the approach you choose.
Ultimately, understanding your options empowers you to protect your personal data effectively.