Activate Glove Mode on a Samsung Galaxy Device is your comprehensive guide to harnessing this handy feature. This mode allows for precise touch interactions even with gloves on, dramatically improving usability in cold weather or while wearing protective gear. We’ll delve into the specifics, from enabling the mode on various Samsung Galaxy devices to troubleshooting common issues and exploring its advanced usage.
This detailed guide covers everything from basic setup to advanced techniques, empowering you to maximize the potential of Glove Mode on your Samsung Galaxy device. We’ll explore how it compares to other input methods like styli or fingers, highlighting its advantages and limitations. Expect clear instructions and practical examples throughout.
Introduction to Glove Mode
Glove Mode, a feature available on select Samsung Galaxy devices, is designed to enhance the user experience when interacting with the device using gloved hands. This innovative technology recognizes and adapts to the unique input characteristics of wearing gloves, making navigation and operation more intuitive and efficient.Glove Mode intelligently processes input from gloved fingers, allowing for smoother scrolling, precise taps, and overall interaction with the screen, even in cold or inclement weather.
The feature addresses the common problem of touch input inaccuracy when wearing gloves, a challenge particularly relevant for outdoor activities or when using the device in colder environments.
Glove Mode Functionality
Glove Mode’s primary function is to improve the accuracy and responsiveness of touch input when gloves are worn. It achieves this by analyzing the pressure and movement patterns of gloved fingers on the screen, recognizing the intent behind the user’s actions, and translating them into appropriate commands. This refined input method minimizes the frustration often associated with touchscreens in cold or gloved conditions.
Figuring out how to activate Glove Mode on your Samsung Galaxy device can be a game-changer for those chilly winter days, especially when you’re trying to navigate through menus without fumbling. Recently, though, I stumbled upon a fascinating story about the Recording Academy settling a dispute with Deborah Dugan, which highlights how these seemingly unrelated events can impact our daily lives in unexpected ways.
Regardless, getting that Glove Mode up and running is a small victory, and something to be appreciated.
Scenarios Where Glove Mode is Helpful
Glove Mode proves particularly useful in a variety of situations. For instance, it enhances the user experience during outdoor activities like skiing, snowboarding, or simply navigating the device while wearing gloves in cold weather. Similarly, it’s advantageous for users with hand conditions that might require wearing gloves or for anyone who frequently operates their device while wearing gloves.
Advantages of Glove Mode Compared to Regular Touch Input
Using Glove Mode offers several advantages over regular touch input. The primary advantage is enhanced accuracy and responsiveness, leading to fewer errors and a more efficient user experience. This is especially true when dealing with fine-tuned actions like scrolling or selecting small elements on the screen, which are more challenging with traditional touch input when wearing gloves.
Examples of Improved User Experience
Glove Mode demonstrably improves user experience by enabling smoother scrolling through menus and web pages. Precise selection of icons and buttons is also simplified, eliminating the need for multiple attempts. The intuitive nature of Glove Mode translates into a more enjoyable and efficient interaction with the device, regardless of the weather conditions or the type of gloves worn.
Samsung Galaxy Device Glove Mode Compatibility
| Device Model | Glove Mode Compatibility |
|---|---|
| Galaxy S23 Ultra | Yes |
| Galaxy S22 Ultra | Yes |
| Galaxy S21 Ultra | Yes |
| Galaxy Note 20 Ultra | Yes |
| Galaxy Z Fold 4 | Yes |
| Galaxy A53 | No |
| Galaxy A73 | No |
| Galaxy A33 | No |
This table provides a concise overview of the Glove Mode compatibility for various Samsung Galaxy devices. Note that compatibility may vary depending on the specific software version. Check the device’s specifications for the most up-to-date information.
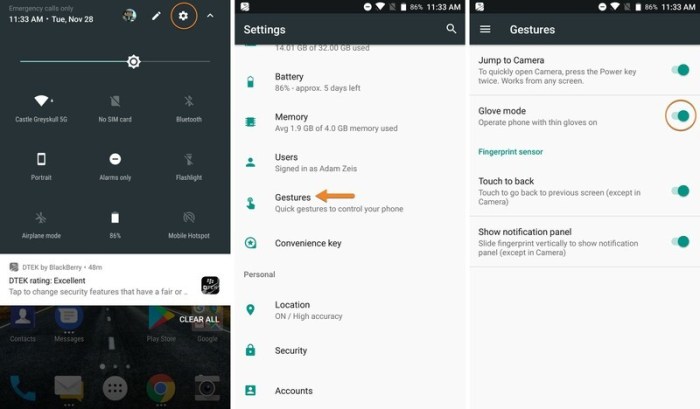
Enabling Glove Mode
Glove Mode on Samsung Galaxy devices is a handy feature designed to enhance touch responsiveness when wearing gloves. This feature adjusts the sensitivity and pressure required for touch interactions, making it easier to use your phone in cold weather or when wearing gloves. Understanding how to activate and configure Glove Mode is crucial for optimal functionality.
Activation Steps on Various Devices
The activation process for Glove Mode is generally consistent across different Samsung Galaxy devices. However, the exact menu structure might vary slightly. The key is to locate the accessibility options within the settings. This section will demonstrate a typical procedure for enabling Glove Mode, using the Samsung Galaxy S23 as an example.
Enabling Glove Mode on Samsung Galaxy S23
To activate Glove Mode on your Samsung Galaxy S23, navigate through the device’s settings menu. The following table Artikels the steps:
| Step | Action |
|---|---|
| 1 | Open the Settings app. |
| 2 | Navigate to the Accessibility section. |
| 3 | Select the “Touch” option. |
| 4 | Look for the “Glove Mode” toggle. |
| 5 | Turn the toggle to “ON”. |
Glove Mode Sensitivity Settings
Proper Glove Mode sensitivity is crucial for optimal performance. Adjusting these settings ensures a seamless experience, avoiding issues like inaccurate touch inputs. Sensitivity settings are typically found within the Glove Mode options menu.The levels of sensitivity often range from low to high. A lower sensitivity setting might be ideal for thick gloves, whereas a higher sensitivity setting might be preferred for thinner gloves.
Experimentation with different settings is essential to find the best balance for your needs.Samsung Galaxy devices offer adjustable sensitivity levels. By fine-tuning these parameters, users can customize the pressure required for actions to be recognized, enhancing overall usability. The specific terminology used for these adjustments may vary across models, but the core concept remains the same.
Glove Mode Features and Settings
Glove Mode is designed to enhance the usability of Samsung Galaxy devices for users wearing gloves. This mode recognizes the different pressure points and movements typical of gloved fingers, allowing for more precise and reliable interaction with touchscreens. This is particularly beneficial for individuals who need to use their devices while wearing gloves, such as those in cold weather or those who work in specific environments requiring protective gear.Glove Mode offers a range of sensitivity options, allowing users to fine-tune the touch response to their specific needs and the type of glove they are wearing.
Adjusting the sensitivity settings is straightforward and can significantly improve the overall user experience. Understanding the responsiveness differences between Glove Mode and standard touch input is crucial to effectively utilize this feature.
Key Features of Glove Mode
Glove Mode is designed to interpret the pressure and motion patterns unique to gloved fingers. This allows users to interact with touchscreens with a higher degree of accuracy and precision than with regular touch input, especially when wearing thick gloves. It provides a more intuitive and responsive experience in cold weather or when working with protective gear.
Ever wanted to use your Samsung Galaxy device with gloves on? Activating Glove Mode is a simple solution, making touchscreen interactions much easier. Speaking of amazing achievements, it’s pretty cool that John Coltrane’s A Love Supreme just went platinum 56 years after its release! This timeless jazz classic is a testament to enduring artistry, much like the simple elegance of Glove Mode, which makes navigating your phone in winter a breeze.
So, next time you’re out in the cold, remember Glove Mode!
Sensitivity Options and User Experience
The sensitivity settings in Glove Mode are crucial for optimizing the user experience. Different glove types and thicknesses will require varying sensitivity levels. Lower sensitivity settings often result in fewer false touches and improved accuracy when dealing with thicker gloves. Higher sensitivity settings, on the other hand, allow for more precise control, potentially improving responsiveness for thinner gloves.
Experimentation with different settings is essential to find the optimal level for a given user and glove combination.
Responsiveness Comparison
Glove Mode’s responsiveness is significantly different from standard touch input. While regular touch input is immediate and direct, Glove Mode often requires slightly more pressure and a more deliberate touch to register the input accurately. This difference is especially noticeable with thicker gloves, where the increased pressure is necessary for the device to correctly identify the touch. The increased responsiveness of Glove Mode in colder weather or when working with protective gear is due to the improved accuracy in interpreting the subtle pressure and movement patterns of gloved fingers.
Potential Issues with Glove Mode
One potential issue with Glove Mode is that it might not accurately register touches in all situations. This can be especially true with very thick gloves, where the pressure needed to activate the touchscreen might be higher than expected. Another potential issue could be that the sensitivity settings might need adjustment for different types of gloves or weather conditions.
Users might need to experiment with different sensitivity levels to find the optimal setting for their specific needs.
Adjusting Glove Mode Sensitivity Settings
Adjusting the sensitivity settings within Glove Mode is straightforward. Users can typically access these settings through the device’s system settings menu. The exact location may vary slightly depending on the specific Samsung Galaxy device model. Users can then experiment with different sensitivity levels to find the optimal setting for their use case.
Glove Mode Sensitivity Levels and Touch Response, Activate Glove Mode on a Samsung Galaxy Device
| Sensitivity Level | Touch Response |
|---|---|
| Low | Fewer false touches, improved accuracy with thick gloves, potentially slower response time. |
| Medium | Balanced response time and accuracy, suitable for a wider range of glove types and thicknesses. |
| High | More precise control, potentially faster response time, but increased risk of false touches with thicker gloves. |
Troubleshooting Glove Mode
Glove Mode, while a helpful accessibility feature, can sometimes encounter hiccups. This section dives into common problems and provides solutions to ensure a smooth experience using Glove Mode on your Samsung Galaxy device. Understanding these issues and their fixes can save you time and frustration.Troubleshooting Glove Mode is essential for maximizing its benefits and ensuring seamless operation. A well-defined troubleshooting process helps identify the root cause of problems, leading to effective solutions.
Common Glove Mode Activation Issues
Activation problems can stem from various factors, including device settings, software conflicts, or even physical interference. Sometimes, a simple restart or a check of your device’s settings can resolve the issue.
- Device not recognizing glove input: The device might not be accurately detecting the glove as an input device. This could be due to issues with the glove’s material or sensors, or perhaps a software glitch. Ensure your glove is properly positioned on your hand and that there are no obstructions.
- Glove Mode activation fails: Activation failures can stem from a variety of causes. Check if the Glove Mode setting is correctly enabled within the device’s accessibility options. Ensure there are no other applications or settings conflicting with Glove Mode.
Glove Mode Responsiveness Problems
Sluggish or unresponsive Glove Mode can be frustrating. Several factors can influence the responsiveness, including system resources, background processes, and even the type of glove used.
- Delayed or inaccurate responses: A delay between input and response might indicate a system overload. Close any unnecessary applications, and ensure your device has sufficient battery power. If the issue persists, a software update might resolve the problem.
- Unresponsive touch inputs: If touch inputs become unresponsive, even outside Glove Mode, it might be a hardware or software issue. Check for any recent software updates that might have introduced problems. Restarting your device can often resolve temporary glitches.
Troubleshooting Glove Mode Activation
Troubleshooting activation problems requires a systematic approach. By following these steps, you can isolate the source of the issue and implement an appropriate solution.
- Check Glove Mode settings: Ensure Glove Mode is correctly enabled within the device’s accessibility settings. Double-check any associated options or configurations.
- Restart the device: A simple restart can resolve minor software glitches that may be interfering with Glove Mode activation. This is a common first step in troubleshooting.
- Update device software: Check for and install any available software updates. New updates frequently include bug fixes and performance improvements, which might address issues with Glove Mode.
Hardware or Software Conflicts
External factors such as hardware compatibility and software conflicts can affect Glove Mode functionality.
- Incompatible hardware: Certain gloves or glove materials may not be compatible with the device’s sensors. Try using a different glove or checking compatibility with other devices.
- Conflicting applications: Some applications might interfere with Glove Mode’s operation. Try closing or disabling any applications that might be conflicting with Glove Mode.
Checking for Software Updates
Software updates are crucial for improving Glove Mode performance.
Ever wished you could use your Samsung Galaxy device with gloves on? Activating Glove Mode is a simple setting that can make a huge difference. It’s a lifesaver in the cold months, or if you just happen to be wearing mittens. Speaking of musical releases, did you hear about porno for pyros share agua their first new song in 26 years?
It’s awesome! Seriously, check out the new track on their website porno for pyros share agua their first new song in 26 years listen. It’s great to see this band back in action. Thankfully, activating Glove Mode is just as simple as adjusting the screen’s sensitivity to suit your gloved hands.
- Regular software updates: Samsung frequently releases updates to improve device functionality. Ensuring your device has the latest software can resolve issues and optimize Glove Mode performance.
- Update method: Use the device’s settings to check for available updates and install them as needed.
Common Glove Mode Problems and Solutions
| Problem | Solution |
|---|---|
| Glove Mode not activating | Check Glove Mode settings, restart the device, update software. |
| Delayed or inaccurate responses | Close unnecessary applications, ensure sufficient battery power, check for software updates. |
| Unresponsive touch inputs | Restart the device, check for software updates, ensure no hardware issues. |
| Incompatible glove | Try a different glove or check for compatibility information. |
Glove Mode vs. Other Input Methods
Glove Mode represents a novel approach to interacting with a Samsung Galaxy device, relying on hand gestures for control. However, it’s not a replacement for all input methods. Understanding its strengths and limitations, along with comparison to existing options like stylus and finger touch, is crucial for maximizing its potential.This section delves into the comparative advantages and disadvantages of Glove Mode, stylus input, and finger touch, highlighting specific situations where each method excels.
It also explores the limitations of Glove Mode, emphasizing the contexts where other methods are more suitable.
Comparison of Input Methods
Understanding the strengths and weaknesses of each input method is essential for choosing the most appropriate tool for the task. Glove Mode, while innovative, is not a universal solution.
- Glove Mode: This method leverages hand gestures for interaction, allowing for intuitive control in specific scenarios. It’s particularly well-suited for tasks where precise finger movements are unnecessary, like navigating menus or controlling playback.
- Stylus Input: Stylus input excels at providing precise control, essential for tasks requiring fine detail. This is advantageous for tasks such as drawing, sketching, or annotating documents.
- Finger Touch Input: Finger touch remains the most common input method, offering a familiar and intuitive way to interact with the device’s interface. It’s ideal for quick tasks like typing, scrolling, or tapping buttons.
Advantages and Disadvantages of Each Method
Different input methods have their own strengths and weaknesses, making them suitable for various tasks.
| Input Method | Advantages | Disadvantages |
|---|---|---|
| Glove Mode | Intuitive for gesture-based actions, potentially faster for certain tasks like navigation, reduced hand fatigue for extended use. | Less precise than stylus or finger touch, not ideal for tasks requiring fine motor control, may not be as familiar to all users. |
| Stylus Input | Exceptional precision, ideal for drawing, sketching, and note-taking, allows for nuanced input. | Can be cumbersome for simple tasks, requires a stylus, potentially slower than finger touch for general interaction. |
| Finger Touch Input | Familiar and intuitive, fastest for most basic tasks, widely accessible. | Limited precision for detailed tasks, prone to accidental touches, can lead to hand fatigue with extended use. |
Situations Favoring Glove Mode
Glove Mode shines in situations where hand gestures are more efficient and natural than precise finger movements.
- Navigation: Glove Mode’s gesture-based approach can be faster for navigating complex menus or presentations, especially on large screens.
- Media Control: Controlling playback, changing volume, or skipping tracks with hand gestures is often more intuitive than using buttons.
- Gaming: Some games may leverage glove mode for specific in-game controls, offering an alternative to traditional controllers or touch input.
Limitations of Glove Mode
Despite its advantages, Glove Mode has limitations compared to other methods.
- Precision: Hand gestures lack the precision of a stylus or direct finger touch, making tasks requiring intricate details difficult.
- Learning Curve: Mastering glove mode gestures takes practice, and users might find it less intuitive than familiar touch input initially.
- Compatibility: Not all apps or interfaces are optimized for glove mode, limiting its usability in specific situations.
Advanced Glove Mode Usage
Glove Mode on Samsung Galaxy devices offers a unique way to interact with your phone. While the basic functionality is straightforward, maximizing its potential requires understanding advanced techniques and configurations. This section dives deep into optimizing Glove Mode performance, exploring its capabilities with specific apps, and highlighting scenarios where it significantly boosts productivity.Advanced Glove Mode usage goes beyond the initial setup.
It involves tailoring the experience to your specific needs and interactions, leveraging advanced settings to refine the touch sensitivity and responsiveness for more precise and efficient input.
Optimizing Glove Mode Performance
Glove Mode performance can be significantly improved by adjusting the touch sensitivity and responsiveness. Overly sensitive settings might lead to unintended inputs, while less sensitive settings could result in sluggish interactions. Finding the optimal balance is crucial. Fine-tuning these settings allows for a more controlled and accurate input experience, minimizing errors and maximizing efficiency.
Advanced Settings and Configurations
Numerous advanced settings within Glove Mode offer granular control over the user experience. These settings allow for precise calibration and adjustments for optimal performance. Understanding and leveraging these settings can lead to a more tailored and effective interaction with the device. Below is a table outlining some key configurations:
| Setting | Description | Example Impact |
|---|---|---|
| Touch Sensitivity | Adjusts the pressure required to register a touch. | Higher sensitivity: more responsive but prone to accidental inputs. Lower sensitivity: less responsive but more accurate for deliberate actions. |
| Responsiveness | Controls the delay between touch and action. | Higher responsiveness: faster input, but may feel less refined. Lower responsiveness: smoother interaction, but may feel slightly slower. |
| Gesture Recognition | Affects the accuracy of gestures. | Precise gesture recognition is crucial for actions like scrolling or zooming. |
| Input Method | Specifies the primary method of input. | Allows for the use of Glove Mode with various applications. |
Glove Mode with Specific Apps
Certain apps benefit significantly from Glove Mode, particularly those requiring precision or extended interaction with on-screen elements. Note-taking apps, drawing tools, and graphic design applications are prime examples where Glove Mode’s accuracy can boost efficiency.
Improving Productivity and Efficiency
Glove Mode excels in situations requiring precision, such as detailed sketching, note-taking, or navigating complex menus. By reducing the reliance on fine motor skills, Glove Mode can improve accuracy and speed in these tasks. Furthermore, its effectiveness varies across different applications and user needs.
Practical Applications
Consider a user needing to navigate a complex spreadsheet. By employing Glove Mode, they can precisely select cells and input data without the need for precise finger placement. This improves efficiency compared to traditional touch input. Similarly, a user who prefers drawing or sketching on their device will find Glove Mode an invaluable tool for precise and fluid creation.
Last Word: Activate Glove Mode On A Samsung Galaxy Device
In conclusion, Glove Mode significantly enhances the usability of your Samsung Galaxy device when wearing gloves. This guide has equipped you with the knowledge to master this feature, from simple activation to advanced configurations. Whether you’re a seasoned tech user or a newcomer, understanding Glove Mode can transform your device interaction, especially in specific situations. Remember to explore the various sensitivity options and troubleshoot any issues that may arise, allowing you to fully utilize this convenient feature.