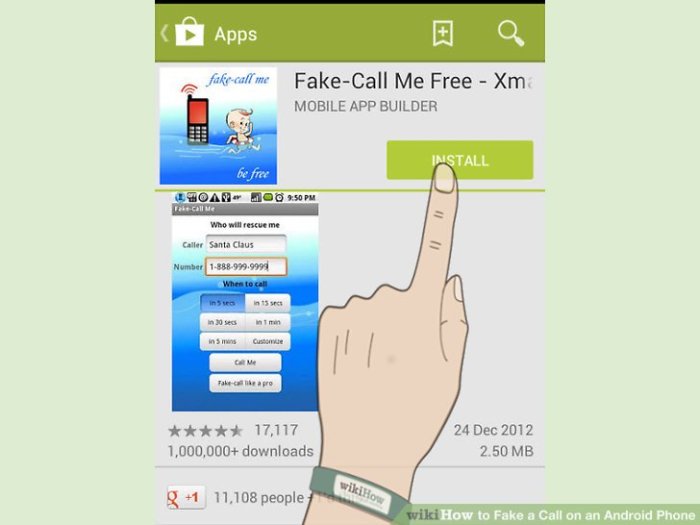
Fake a Call on an Android Phone explores the fascinating world of call-faking apps and techniques. From harmless pranks to more complex applications, understanding the motivations, methods, and potential risks is crucial. This detailed guide delves into the technical aspects, security concerns, and even the ethical considerations behind creating and using these applications.
We’ll examine the various methods available, from simple app-based solutions to more sophisticated system-level approaches. We’ll also analyze the pros and cons of each, considering factors like user experience, potential security vulnerabilities, and the legal landscape surrounding this practice.
Introduction to Fake Calls on Android: Fake A Call On An Android Phone
Faking a phone call on an Android device is a feature that allows users to simulate an incoming call, often displaying a caller ID and initiating a call-like experience without an actual person on the other end. This capability is readily available through various apps and functionalities. Understanding the motivations behind its use is key to comprehending its impact.This functionality is employed for a diverse range of purposes, ranging from harmless pranks to more serious applications, such as avoiding unwanted calls.
Its versatility stems from the ability to customize the caller ID and other aspects of the simulated call.
Common Motivations
Users employ fake call functionality for a multitude of reasons. Understanding these motivations helps appreciate the nuanced ways this technology is used. The motivations often fall into two broad categories: playful and practical.
Different Uses of Fake Call Functionality
This feature can be used for a variety of purposes, including but not limited to harmless pranks, avoiding unwanted calls, and creating unique experiences. The potential applications are vast, showcasing the adaptability of this technology.
| Motivation | Example Use Case |
|---|---|
| Pranks | Tricking a friend into believing a celebrity is calling them. |
| Avoiding Unwanted Calls | Simulating a call from a trusted contact to deflect a telemarketer. |
| Creating Unique Experiences | Simulating a call from a fictional character for entertainment. |
| Testing Communication Systems | Simulating calls from various numbers to test call routing or software response. |
Brief History
The practice of faking phone calls likely emerged alongside the widespread availability of mobile phones. Early applications and modifications likely enabled users to simulate calls for various purposes, evolving with technological advancements and user needs. The sophistication of these applications has grown alongside mobile operating systems, becoming increasingly user-friendly and versatile.
Methods for Faking Calls
Faking incoming calls on an Android device has become increasingly popular, offering various use cases from harmless pranks to more sophisticated applications. Understanding the methods available allows users to make informed decisions about the security implications and potential misuse of such tools. The proliferation of apps designed for this purpose necessitates a critical approach to their use and potential risks.Faking calls on Android devices is achievable through a variety of methods, each with its own strengths and weaknesses.
The choice of method depends on the user’s specific needs and the desired level of realism. Understanding these methods can help users navigate the world of call-faking apps and understand the implications of their use.
App-Based Methods
Several applications are specifically designed to simulate incoming calls on Android. These apps vary in their features and capabilities, allowing for customization and personalization of the faked call.
- Call Simulation Apps: These apps provide a straightforward way to create and manage fake calls. They often allow users to specify the caller ID, contact name, and even the call duration. Some apps even permit the playback of pre-recorded messages or audio files to enhance the realism of the simulated call.
- Prank Apps: This category of apps focuses on entertainment and often includes features for creating humorous or entertaining fake calls. These applications are frequently used for pranks and lighthearted fun, but they may not offer the same level of customization as call simulation apps.
- Customization Options: Many call-faking applications allow users to adjust various aspects of the simulated call, such as the caller’s name, number, call duration, and even the type of audio played during the call. These options provide users with a degree of flexibility to tailor the fake call to their needs or desired outcome.
System-Level Methods, Fake a Call on an Android Phone
While app-based methods are prevalent, some users explore more advanced system-level techniques. These methods typically involve modifying the device’s operating system or utilizing specialized tools.
- Root Access: Accessing root privileges on an Android device grants the user a high level of control. With root access, users can potentially alter the phone’s call routing or modify system files to simulate incoming calls. However, this method is often complex and may void the device’s warranty.
- Custom ROMs: Using custom ROMs can allow users to implement modified call handling logic. These ROMs are often developed by the community and can provide a more extensive array of features than typical Android ROMs. However, the installation and configuration of custom ROMs may be complex and require technical expertise.
Comparison of Methods
| Method Name | Description | Pros | Cons |
|---|---|---|---|
| App-Based | Simulates incoming calls using dedicated applications. | Ease of use, readily available, often customizable. | Limited control over system-level interactions, potentially less realistic compared to system-level methods. |
| System-Level | Modifies the operating system to simulate calls. | Potentially more realistic and customizable control. | Requires technical expertise, risk of device damage or malfunction, voiding warranty. |
Technical Aspects
Faking calls on Android, while seemingly simple, relies on intricate interactions within the operating system. Understanding these technical mechanisms is crucial for both appreciating the process and recognizing potential security vulnerabilities. This section delves into the underlying technical processes, the affected Android components, and the potential for malicious exploitation.The core of faking a call involves manipulating Android’s telephony stack, a complex system responsible for handling all communication tasks, including incoming and outgoing calls.
This manipulation often involves bypassing standard call routing procedures and injecting synthetic call events. Android’s architecture, designed for security and stability, makes such manipulations challenging, but not impossible. These manipulations, when successful, can create a deceptive experience for both the caller and recipient.
Underlying Mechanisms
Android’s telephony stack is a layered system, with each layer responsible for specific tasks. These layers interact to process and manage call events. Faking calls typically involves targeting specific components within this stack to inject false call information. For instance, manipulating the call state reporting, or intercepting the network requests related to a call can create a false call.
Affected Android System Components
Several Android system components are crucial to the telephony stack and therefore potentially affected by call-faking applications. The interaction and manipulation of these components is key to achieving the desired outcome.
- Telephony Manager: This service acts as the central hub for managing telephony-related operations. Manipulating the Telephony Manager allows an application to control the call state, potentially hiding or redirecting incoming or outgoing calls.
- Phone App: The native phone application is a crucial component, as it handles the UI for call management. Any manipulation of the phone app’s internal state can deceive the user into believing a call is occurring when it is not.
- Network Interface: The network interface is vital for establishing and managing the communication channels during a call. Intercepting or modifying these communication channels allows for the creation of fake call events.
- Call State Handling: This aspect of the system manages the various states a call can be in (ringing, connected, etc.). Manipulating the call state transition can lead to a false representation of a call in progress.
Potential Malicious Exploitation
The techniques used to fake calls can be exploited for malicious purposes. A malicious application could potentially use these methods to:
- Phishing and Scams: A fake call could lead to a victim revealing sensitive information, such as bank account details or passwords.
- Identity Theft: By spoofing a legitimate entity’s number, a malicious actor can trick the victim into believing they are communicating with a trusted party.
- Harassment and Bullying: Fake calls can be used to harass or intimidate individuals, creating a significant psychological impact.
Technical Steps in Creating a Fake Call Application
Creating a fake call application involves several steps. While the exact implementation details are complex, the general approach involves manipulating the Android telephony stack through code.
- Code Implementation: The application code needs to interact with the Telephony Manager and other relevant APIs to modify the call state.
- Event Injection: The application needs to inject simulated call events into the system. This usually involves mimicking the signals and data exchanged during a normal call.
- UI Simulation: To provide a realistic user experience, the application needs to simulate the visual elements of an incoming call. This includes displaying a call notification, and creating a call window on the screen.
- Permissions Management: A fake call app typically needs specific permissions to access and manipulate telephony features. Carefully managing these permissions is crucial.
Vulnerability Analysis
The following table summarizes the components affected by fake call applications and their vulnerability potential.
Ever wanted to prank a friend with a fake call on your Android? It’s surprisingly easy, but if you’re looking for something a little more sophisticated, maybe you’d appreciate the resurgence of well-tailored suits in the summer style. Suits makes summer return is a major trend, showing that even the fashion world is embracing the versatility of style.
Regardless, a fake call app can be a great tool for fun and practical purposes. It’s a simple way to add a touch of whimsy to your day, or even help you avoid an awkward conversation.
| Component | Role in Faking Calls | Vulnerability Potential |
|---|---|---|
| Telephony Manager | Central hub for telephony operations | High; manipulation can bypass normal call routing |
| Phone App | Handles UI for call management | Medium; modification can lead to misleading UI |
| Network Interface | Establishes and manages communication | High; intercepting/modifying network traffic allows for false call generation |
| Call State Handling | Manages call states | High; manipulating call states creates a deceptive experience |
Security and Privacy Concerns
Fake call apps, while seemingly harmless, can pose significant security and privacy risks. Users should be aware of the potential vulnerabilities and the different levels of risk associated with various methods. The ease of access to these applications often overshadows the potential dangers, leading to a lack of caution from users.
Potential Security Risks
The proliferation of fake call apps creates a breeding ground for malicious actors. Compromised applications can potentially steal personal information, or worse, grant unauthorized access to devices. These apps might include hidden malware or exploit vulnerabilities in the operating system to gain unauthorized access to sensitive data. A common security risk involves the possibility of unknowingly installing apps with malicious intent.
These apps may collect user data without consent or even without the user’s knowledge, potentially leading to identity theft or financial loss.
Privacy Concerns
Privacy concerns arise from the very nature of faking calls. Applications often require access to sensitive data to function, raising red flags about data collection and potential breaches. This data may include contacts, call logs, and other personal information, which could be exploited for malicious purposes. The data collected may be shared with third-party entities without explicit user consent, further jeopardizing privacy.
The potential for data breaches is always a concern when dealing with personal data collection, and fake call apps are no exception.
Specific Method Risks
The methods used to create fake calls influence the associated risks. For example, apps relying on voice synthesis to create calls may have varying degrees of success in masking the caller’s identity. However, sophisticated detection methods can reveal the authenticity of the call. Using a pre-recorded message as a fake call presents the risk of the caller’s identity being compromised.
Legal Implications
Using fake call applications may have legal implications depending on the jurisdiction and the specific actions taken. For example, using fake calls to harass or impersonate someone is illegal in most places. The use of fake calls for fraudulent activities, like phishing scams, also carries significant legal consequences. The legal landscape surrounding fake call apps is constantly evolving, making it crucial to be aware of the local regulations.
Structured List of Risks
- Data breaches: Fake call apps may collect and store user data, potentially leading to breaches and exposing sensitive information. This includes personal contact lists, call logs, and potentially other data.
- Malware: Some applications may contain hidden malware, enabling malicious access to user devices and potentially leading to the compromise of personal accounts or financial information.
- Identity theft: Collected data can be used for identity theft, allowing malicious actors to impersonate users for fraudulent activities.
- Financial fraud: Fake calls can be used for phishing scams or other fraudulent activities, potentially leading to financial losses.
- Harassment and impersonation: Using fake calls to harass or impersonate others is illegal in most jurisdictions.
- Violation of privacy laws: Unauthorized data collection and sharing without explicit consent violate privacy laws in many jurisdictions.
Legal and Ethical Considerations
The use of fake call applications raises significant legal and ethical questions, varying considerably across different jurisdictions. Understanding these implications is crucial for both developers and users to navigate the potential pitfalls and ensure responsible use. The lines between harmless fun and potentially harmful misuse can be blurry, necessitating careful consideration of the consequences.
Legal Implications of Fake Call Applications
The legality of using fake call applications is heavily dependent on local laws and regulations. Some jurisdictions might view such applications as harmless entertainment tools, while others might perceive them as potentially misleading or even malicious. This can lead to varied interpretations and enforcement of the law, creating ambiguity and uncertainty. For example, using a fake call app to impersonate a legitimate authority figure could be considered a form of fraud in many places.
Ever wanted to prank a friend with a fake call on your Android phone? It’s surprisingly easy, but it’s also fascinating how similar that feeling is to the half-hearted love explored in Clare Maguire’s piece clare maguire half hearted love. Maybe it’s the subtle hesitation, the lingering doubts, that make these digital charades so relatable. Regardless, knowing how to fake a call is still a useful skill for those playful moments.
Ethical Considerations Surrounding Fake Call Applications
Beyond the legal implications, ethical considerations are also crucial. The use of fake call applications raises concerns about privacy, deception, and the potential for harm. Using such applications to mislead or deceive others, especially for personal gain or malicious intent, is clearly unethical. Furthermore, the potential for misuse, such as harassment or stalking, necessitates careful consideration of the ethical boundaries.
Comparison of Legal and Ethical Implications Across Countries
The legal and ethical implications of fake call applications differ significantly across countries and regions. Cultural norms, societal values, and legal frameworks all contribute to the varying perspectives on the acceptable use of such technology. For instance, a practice considered harmless entertainment in one country might be viewed as a serious offense in another.
Table of Legal and Ethical Considerations
| Country/Region | Legal/Ethical Considerations |
|---|---|
| United States | The legality of using fake call apps is often determined on a case-by-case basis, considering the specific context and intent behind the use. Misuse for fraudulent activities, harassment, or impersonation could lead to legal repercussions. Ethical considerations emphasize the importance of avoiding deception and harm to others. |
| European Union | EU regulations regarding data privacy and consumer protection could impact the use of fake call apps. The potential for misuse, such as impersonating individuals or entities for fraudulent purposes, raises ethical concerns. Specific laws might prohibit certain actions based on context and intent. |
| China | Regulations in China regarding technology and user behavior may place limitations on fake call apps, especially if they are deemed to facilitate fraudulent activities or social disruption. Ethical considerations in China often emphasize social responsibility and maintaining order. |
| India | Laws in India may vary depending on the intended use of the fake call application. If the application is used for fraudulent purposes, it could be considered illegal. Ethical concerns often center on respecting privacy and avoiding the potential for harm. |
User Experiences
Fake call apps, while seemingly innocuous, offer a fascinating glimpse into user behavior and the nuances of mobile interaction. Understanding the typical user experience, including common issues and application usability, provides valuable insight into the app’s practical value and potential pitfalls. This section delves into the day-to-day usage of these apps, examining their strengths and weaknesses from a user perspective.
Typical User Flow
The typical user journey for a fake call application usually begins with downloading and installing the app. After successful installation, users are often greeted with an intuitive interface that allows them to easily select a contact from their phone’s contacts list or choose from pre-populated options. Next, users customize the incoming call details, such as the caller’s name and number.
Finally, the user initiates the call simulation, which typically involves triggering a simulated incoming call alert.
Common Issues
Users frequently encounter issues with call quality and accuracy. Sometimes the simulated call may not accurately mimic a real phone call, leading to frustration. Problems can also arise from the app’s ability to handle background processes or multitasking. Inconsistent compatibility across different Android devices and versions is another common concern, leading to unexpected results or app crashes.
Ever wanted to fake a call on your Android phone? It’s surprisingly easy to do, but you might be more interested in the intense visuals of Death Grips’ short film “For Come Up and Get Me Shot Last Year at Chateau Marmont” here. Regardless of your interest in that, if you’re looking for a fun little Android trick, there are plenty of apps to help.
Plenty of creative ways to fake calls exist for Android phones.
Poor call simulation can result in a jarring user experience, and sometimes the fake call may not be visually or audibly distinct from a real call, causing confusion.
Comparison of Applications
Various fake call apps offer distinct user experiences. Some applications boast user-friendly interfaces with intuitive controls, allowing users to customize calls with ease. Other applications might present a more complex interface with numerous options, potentially overwhelming users. The quality of the simulated call audio and visual cues also varies significantly. Factors such as compatibility with various Android versions and the app’s ability to handle multitasking significantly impact the overall user experience.
For instance, some apps may struggle to maintain smooth operation during intensive tasks, resulting in a noticeably laggy user experience.
Usability of Fake Call Applications
The usability of fake call applications can be evaluated based on factors like ease of navigation, clarity of instructions, and the app’s ability to meet user needs. Applications that provide clear instructions, well-organized layouts, and a consistent user interface tend to be more usable. A good app allows for straightforward customization and simulation of incoming calls, and a good fake call app should also have a minimal number of unexpected behavior, ensuring a positive user experience.
“A typical user flow involves downloading, selecting a contact, customizing the call details, and initiating the simulated call.”
Examples of Fake Call Applications
Fake call apps have become a popular way to deal with various situations, from avoiding unwanted calls to having fun with friends. Understanding the different types of applications and their features can help users choose the best option for their needs. This section delves into some popular fake call apps, analyzing their strengths and weaknesses.
Popular Fake Call Applications
A variety of apps offer the ability to simulate incoming calls. Choosing the right one depends on specific requirements, like the desired features and the level of control needed. Several applications cater to diverse needs and preferences, providing a variety of options for users.
- Fake Call: This app is a straightforward solution for faking calls. It allows users to set up a simulated call with a customizable caller ID and the ability to pre-record a message to play during the call. This app is relatively simple to use and is a good choice for basic call simulation needs. Users can easily set up a fake call with various features to make the simulation more realistic.
However, it might lack some advanced options compared to other apps.
- Call Simulator: This app offers a more comprehensive approach to faking calls, with a wider range of customization options. Features include customizable caller IDs, pre-recorded messages, and the ability to schedule fake calls in advance. Users can also set different call durations and customize the call tone. This offers flexibility and control, but might require more time to set up compared to simpler apps.
- Fake Call App Pro: This app is often a premium version of a basic fake call app. It usually provides advanced features like the ability to record calls, schedule multiple fake calls, and even customize the call’s appearance. The added features and improved functionalities can be highly valuable to users who need more control over the simulation. The increased features usually come with a price, so users need to evaluate whether the extra features are worth the cost.
- Fake Caller ID: This app focuses specifically on the caller ID aspect. Users can choose a desired caller ID and simulate a call from that number. This can be helpful for various scenarios, such as avoiding unwanted calls or setting up a surprise for someone. The app usually is straightforward and simple to use, making it suitable for those who want to change the caller ID quickly.
However, it may not offer the same level of customization for other call aspects.
Pricing and User Interface
Pricing models for fake call apps vary significantly. Some apps are completely free with limited features, while others offer premium versions with enhanced capabilities. The user interface design also plays a significant role in user experience. Some apps are visually appealing and easy to navigate, while others may be cluttered or difficult to use.
| App Name | Key Features | Pros | Cons |
|---|---|---|---|
| Fake Call | Basic call simulation, customizable caller ID, pre-recorded messages | Simple to use, good for basic needs, free option available | Limited customization options, potentially less realistic compared to others |
| Call Simulator | Wider range of customization, pre-recorded messages, scheduled calls | More control over the simulation, good for variety of use cases | Steeper learning curve, might not be suitable for everyone |
| Fake Call App Pro | Advanced features like call recording, scheduling multiple calls, customizable appearance | Greater control and flexibility, improved realism | Higher cost, might not be necessary for all users |
| Fake Caller ID | Focus on changing caller ID, simple and quick use | Easy to use, ideal for avoiding unwanted calls or surprising others | Limited call simulation features, less control over call details |
Potential Future Developments
The landscape of fake call applications is constantly evolving, driven by advancements in technology and user demand. Predicting the precise trajectory of future developments is challenging, but examining current trends offers insights into potential paths. These applications, once a niche interest, are increasingly intertwined with broader technological shifts.
Emerging Technologies Impacting Fake Call Apps
Advancements in artificial intelligence (AI), particularly in speech synthesis and voice cloning, are poised to revolutionize the accuracy and realism of fake calls. AI-powered voice cloning can create near-perfect imitations of real voices, potentially blurring the lines between authentic and fabricated interactions. This could lead to both innovative applications, like personalized automated assistants mimicking specific individuals, and potentially harmful uses, such as elaborate scams.
Improved natural language processing (NLP) could enable more nuanced and contextually relevant conversations within fake call applications, making them even more convincing.
Advancements in Call-Faking Technologies
Future fake call applications might leverage advancements in augmented reality (AR) to create immersive experiences. Users could potentially be immersed in a simulated environment where the fake call appears as part of a larger, interactive scene. For example, a user might receive a fake call while appearing to be in a virtual office, café, or even a different geographical location.
This technology could transform the user experience beyond simply mimicking a call and into a richer, more interactive environment.
Potential Future Directions for Research
Research in this area could focus on developing robust methods to detect AI-generated calls and identify instances of voice cloning. This would help to mitigate the potential for misuse, particularly in fraud and scams. Additionally, the ethical implications of increasingly realistic voice cloning and the potential for misuse in the context of privacy violations will need careful consideration.
The impact of these applications on social dynamics and interpersonal relationships, including the potential for increased social isolation or manipulation, is a significant area requiring further study.
Potential Future Developments
- AI-Enhanced Voice Cloning: More accurate and realistic voice cloning using AI will likely make fake calls indistinguishable from real ones, raising significant security concerns and prompting the development of anti-cloning technologies.
- AR Integration: Augmented reality integration could create more immersive experiences for fake calls, potentially blurring the lines between the virtual and physical worlds, creating scenarios where a fake call takes place in a virtual environment, adding a layer of realism.
- Advanced NLP for Conversational Realism: Natural Language Processing (NLP) could be used to create more natural and contextually relevant conversations in fake calls, making them more convincing and potentially useful for language learning or practicing different communication styles.
- Improved Detection Technologies: Research will focus on developing more sophisticated methods to identify AI-generated calls and instances of voice cloning, to mitigate the risks associated with fraud and misuse.
- Ethical and Legal Frameworks: The ethical implications of increasingly sophisticated voice cloning and the potential for misuse, including privacy violations, will need careful consideration, leading to the development of specific ethical and legal frameworks for this technology.
Final Summary
In conclusion, faking a call on an Android phone is a multifaceted topic with diverse implications. Understanding the underlying mechanisms, potential risks, and ethical considerations is vital for responsible use. This exploration highlights the interplay between technology, human behavior, and the legal framework surrounding such applications. Whether for harmless fun or more complex purposes, this discussion offers a comprehensive overview of the topic.


Leave a Reply