Remotely Shutdown a Computer is a powerful technique that allows you to control and manage computers from a distance. Whether you need to quickly shut down a machine in a remote office or simply want a more convenient way to manage your home network, understanding the various methods, software, and security considerations is crucial. This guide will explore the ins and outs of remote shutdown, from basic definitions to complex scripting and security best practices.
This comprehensive guide covers everything from the fundamental concepts of remote shutdown to advanced techniques like scripting and automation. You’ll discover how to use various software tools, command-line interfaces (CLI), and network protocols to achieve remote shutdown. Crucially, we’ll delve into the critical aspects of security, ensuring that your remote shutdown procedures are not only effective but also secure.
Introduction to Remote Shutdown
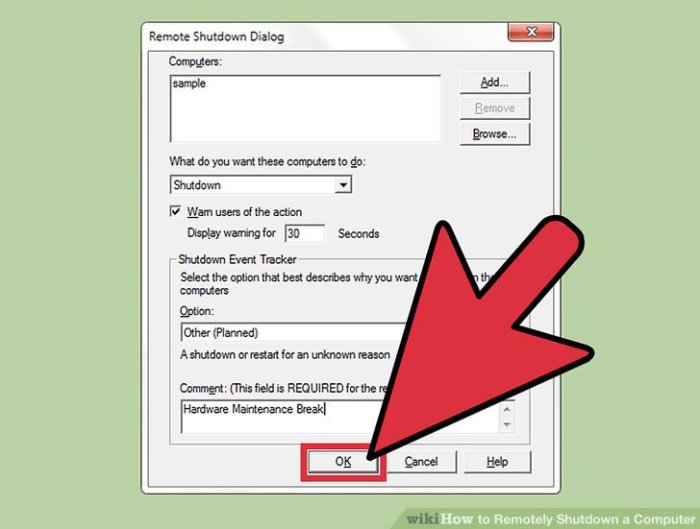
Remotely shutting down a computer involves initiating the computer’s shutdown process from a different location or device. This capability is crucial for system maintenance, troubleshooting, and security. It streamlines administration tasks, allowing IT professionals to manage multiple systems efficiently.This process leverages remote access software, providing a convenient and efficient method to control and manage computer systems remotely. Various methods exist, each with unique advantages and disadvantages, making careful selection essential.
Security is paramount when employing remote shutdown, demanding consideration of potential vulnerabilities.
Remote Shutdown Methods
Various methods facilitate remote computer shutdown. These methods often rely on remote access software to connect to and control the target computer. Direct commands, or software-based systems, can trigger the shutdown process.
Remote Access Software
Numerous software programs enable remote access to computers. These programs facilitate control over the target machine, allowing for a variety of operations, including initiating shutdown. Examples include TeamViewer, AnyDesk, and Remote Desktop Connection. Each offers unique features and security protocols, impacting the overall security posture of the remote shutdown process.
Security Considerations for Remote Shutdown
Security is a critical aspect of remote shutdown. Unauthorized access to a system poses risks, potentially leading to data breaches or system damage. Robust security measures, including strong passwords, secure connections, and access control, are paramount. Implementing multi-factor authentication (MFA) and firewalls can add significant layers of security.
Comparison of Remote Shutdown Methods
| Method | Advantages | Disadvantages | Security Considerations |
|---|---|---|---|
| Remote Desktop Connection (RDP) | Built-in Windows feature, generally stable and reliable, good for familiar Windows environments. | Requires the target computer to be on and have the RDP service enabled. Less user-friendly than dedicated remote access software for non-technical users. | Vulnerable to brute-force attacks if weak passwords are used. Requires secure network connections. |
| TeamViewer | User-friendly interface, widely available, provides robust remote control. | Requires installation on both the remote and local machines, potential for network latency issues. | Security depends on the chosen encryption and access controls. Properly configuring firewall rules is crucial. |
| AnyDesk | Lightweight and fast, low latency, suitable for diverse networks. | Requires installation, potential compatibility issues with specific systems. | Encryption and authentication protocols need careful configuration. |
| Command-line tools (e.g., PowerShell) | High degree of control and automation, especially for scripting. | Requires technical knowledge, potential for errors if not carefully implemented. | Requires secure authentication mechanisms and careful script development to avoid unintended consequences. |
Software-Based Remote Shutdown
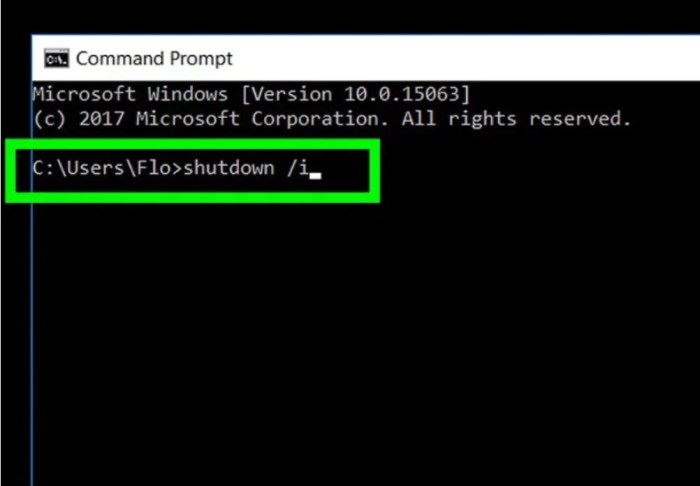
Remotely shutting down a computer is a useful skill for administrators and users alike. Whether it’s for maintenance, troubleshooting, or simply a convenient way to end a session, software-based solutions provide a flexible and often more secure alternative to physical access. This method bypasses the need for direct physical interaction, offering significant advantages in terms of efficiency and control.Software solutions offer a range of features, from simple shutdown commands to more comprehensive management tools.
They also often incorporate security measures to protect against unauthorized access and misuse. Choosing the right software depends on specific needs and security requirements.
Popular Software Solutions
Various software solutions cater to remote shutdown needs. Some popular options include TeamViewer, AnyDesk, and specialized remote administration tools. Each program provides different features and levels of control. Understanding the specifics of these solutions is essential for selecting the best fit.
Comparison of Software Solutions
| Software | Features | Security Protocols | User Interface |
|---|---|---|---|
| TeamViewer | Remote control, file transfer, screen sharing, and remote shutdown. | Strong encryption protocols, including AES-256. Two-factor authentication and access controls. | Intuitive and user-friendly interface, with clear navigation and icons. |
| AnyDesk | Remote control, file transfer, screen sharing, and remote shutdown. Supports a wide range of operating systems. | Robust encryption (AES-256). Strong access controls, user management, and audit trails. | Clean and modern design, straightforward controls, and good performance. |
| DameWare | Comprehensive remote administration, including remote shutdown, file transfer, and more. | Offers encryption, user accounts, and secure remote connections. | Advanced features often necessitate some learning curve for complete control. |
This table provides a basic comparison, highlighting key features, security protocols, and user interface elements. Each solution has its strengths and weaknesses, making it important to consider the specific needs of your setup.
Installation and Setup of TeamViewer
To install and set up TeamViewer, download the appropriate installer for your operating system. Follow the on-screen prompts to complete the installation. Create a TeamViewer account and generate a unique ID and password. This process is crucial for secure remote access. It’s highly recommended to enable two-factor authentication for added security.
Using TeamViewer for Remote Shutdown
After successful installation and setup, launch the TeamViewer application on both the computer you want to control and the computer you are using to control it. Using the ID and password, connect to the target computer. Once connected, navigate to the control panel and locate the option to shut down the remote computer. Execute the shutdown command.
This action will initiate the shutdown process on the target machine.
Scripting and Automation
Automating remote shutdown tasks significantly improves efficiency and reduces manual intervention. Scripting languages provide a powerful mechanism to execute these tasks, enabling streamlined management of computer systems, especially in environments with numerous machines or complex schedules. This approach reduces the likelihood of human error and allows for the execution of tasks that would otherwise be tedious or impossible to manage manually.
PowerShell Scripting for Remote Shutdown
PowerShell, a powerful scripting language built into Windows, offers robust tools for managing remote computers. Its cmdlets (commands) allow for direct interaction with the remote system, enabling the automation of shutdown tasks.
Here’s a basic example of a PowerShell script to remotely shut down a specific computer:
“`powershell# Connect to the remote computer. Replace with the actual computer name.$ComputerName = “MyRemoteComputer”# Use the Stop-Computer cmdlet to initiate the shutdown.Stop-Computer -ComputerName $ComputerName -Force -Confirm:$false“`
This script uses the Stop-Computer cmdlet. The -ComputerName parameter specifies the target machine. The -Force parameter is crucial, ensuring the shutdown process is initiated even if the user is logged in. The -Confirm:$false parameter suppresses the confirmation prompt, which is useful in automated scripts.
Python Scripting for Remote Shutdown
Python, a versatile scripting language, also provides a way to automate remote shutdown tasks. It offers libraries like `paramiko` for secure remote connections, allowing scripts to execute commands on remote machines.
A simple Python script using Paramiko to achieve the same result:
“`pythonimport paramikodef remote_shutdown(hostname, username, password): try: # Establish SSH connection client = paramiko.SSHClient() client.set_missing_host_key_policy(paramiko.AutoAddPolicy()) client.connect(hostname, username=username, password=password) # Execute the shutdown command stdin, stdout, stderr = client.exec_command(“shutdown /s /t 0″) # Check for errors if stderr.read().strip(): print(f”Error shutting down hostname: stderr.read().strip()”) else: print(f”Shutdown initiated for hostname”) client.close() except paramiko.AuthenticationException: print(f”Authentication failed for hostname”) except Exception as e: print(f”An error occurred: e”)# Replace with your credentials and target hostnameremote_shutdown(“MyRemoteComputer”, “administrator”, “yourpassword”)“`
This example utilizes the `paramiko` library to create an SSH connection to the remote computer. It then executes the shutdown command (`shutdown /s /t 0`) within the remote session.
Scheduling Remote Shutdown Tasks
Scheduling remote shutdown tasks can be integrated into the scripts using tools like Task Scheduler (Windows) or cron (Linux/macOS). These tools allow you to define when the shutdown should occur, ensuring tasks are performed automatically.
Scripting Language Comparison
| Language | Key Strengths | Example Script Snippet | Advantages |
|---|---|---|---|
| PowerShell | Built-in Windows, direct cmdlet access, simple syntax | Stop-Computer -ComputerName $ComputerName -Force |
Easy to use for Windows environments, very efficient for remote operations. |
| Python | Versatile, robust libraries (like Paramiko), cross-platform | remote_shutdown("MyRemoteComputer", "administrator", "yourpassword") |
Cross-platform compatibility, powerful for complex automation tasks, great for network management. |
CLI Tools for Remote Shutdown
Command-line interface (CLI) tools offer a powerful and flexible way to remotely shut down computers. They are often preferred for scripting and automation tasks, providing a precise and efficient means to manage remote systems. These tools provide granular control, allowing for specific actions on individual machines or groups of machines, and are fundamental in system administration.
SSH for Remote Shutdown
SSH (Secure Shell) is a versatile tool for secure remote login and command execution. Its primary use in remote shutdown involves using the `shutdown` command.
The `shutdown` command, when used remotely, requires appropriate permissions and access control configurations.
SSH allows for the execution of arbitrary commands on a remote machine. To initiate a remote shutdown, the `shutdown` command is issued to the target machine, specifying the desired action and time. The `-h` option is crucial for initiating a shutdown, and `now` typically initiates an immediate shutdown.Example:“`bashssh user@remote_host “shutdown -h now”“`This command connects to the remote host using SSH, as `user@remote_host`, and executes the `shutdown -h now` command on that machine.
psexec for Remote Shutdown on Windows
psexec is a command-line tool specifically designed for remote execution on Windows systems. It offers a more direct approach to remote shutdown compared to SSH.
psexec facilitates the execution of commands on remote Windows systems.
Using psexec, a shutdown command can be directly sent to a target machine.Example:“`psexec \\remote_machine shutdown -f -s -t 0“`This command shuts down the remote machine (`\\remote_machine`) immediately (`-t 0`). The `-f` option forces the shutdown, even if applications are running, which is often crucial in automated scripts.
Remote Shutdown CLI Tools Summary
| Tool | Parameters | Description | Example ||—|—|—|—|| SSH | `shutdown -h now` | Initiates an immediate shutdown on the remote host. | `ssh user@remote_host “shutdown -h now”` || psexec | `shutdown -f -s -t 0` | Forces a shutdown on the remote Windows machine immediately. | `psexec \\remote_machine shutdown -f -s -t 0` || psexec | `shutdown -f -s -t 30` | Forces a shutdown on the remote Windows machine in 30 seconds.
| `psexec \\remote_machine shutdown -f -s -t 30` |
Network Protocols and Considerations: Remotely Shutdown A Computer
Remotely shutting down a computer relies heavily on the underlying network infrastructure. Understanding the protocols, security implications, and network considerations is crucial for a stable and secure remote shutdown process. Efficient communication and reliable delivery of shutdown commands are paramount, ensuring the target machine receives and executes the command correctly.
Network Protocols for Remote Shutdown
TCP/IP (Transmission Control Protocol/Internet Protocol) is the fundamental suite of protocols used for virtually all internet-based communication. Remote shutdown commands, often packaged within application layer protocols like SSH or custom protocols, travel over the network using TCP/IP. TCP guarantees reliable delivery of data, ensuring the shutdown command reaches the target machine without corruption. IP handles the addressing and routing of the data packets, ensuring the command travels to the correct destination.
The specific protocol used for remote shutdown depends on the chosen method (e.g., software, scripting, or command-line tools).
Network Security and Firewall Rules, Remotely Shutdown a Computer
Network security plays a vital role in protecting systems from unauthorized access. Firewalls act as gatekeepers, controlling the flow of network traffic. Firewall rules dictate which ports and protocols are allowed to communicate. Remote shutdown commands must be explicitly permitted through firewall rules to function correctly. Without proper firewall configuration, the remote shutdown attempt might fail due to blocked communication.
This is crucial for preventing malicious actors from remotely shutting down systems or other unwanted actions.
Importance of Port Forwarding
Port forwarding is a technique used to direct network traffic to a specific machine or service within a network. In remote shutdown scenarios, port forwarding is often necessary to route commands to the target computer. Without port forwarding, the remote shutdown application might not be able to reach the target computer, and the command will fail. This is particularly important in scenarios where the target machine is behind a firewall or a network router.
For example, if the target machine is on a private network, port forwarding on the router allows external connections to reach the target machine on a specific port.
Network Latency and its Impact
Network latency, often measured in milliseconds, refers to the time delay for data to travel across a network. High latency can significantly impact the speed and reliability of remote shutdown commands. The longer it takes for the command to reach the target machine, the longer the shutdown process will take. In some situations, latency might result in a time-out, preventing the shutdown from occurring.
Real-world scenarios, like geographically dispersed networks, can exhibit noticeable latency, affecting the efficiency and reliability of remote shutdown procedures. A low latency connection is ideal to avoid timeouts and ensure a smooth shutdown process.
Network Topologies Supporting Remote Shutdown
Various network topologies can support remote shutdown, each with its own characteristics. The choice of topology depends on the specific requirements of the system. Star topology, where all devices connect to a central hub, provides a centralized control point for remote shutdown commands. Mesh topology, where each device connects to multiple others, offers redundancy and fault tolerance.
In a client-server topology, a central server manages the shutdown requests, improving security and manageability. The specific topology choice depends on the number of devices, security requirements, and other factors. Examples of different topologies and their relative merits in remote shutdown situations should be evaluated based on the specific network and security considerations.
Security Best Practices
Remotely shutting down a computer, while convenient, introduces security vulnerabilities if not implemented correctly. Robust security measures are crucial to prevent unauthorized access and ensure the integrity of the system. This section details vital security best practices to mitigate risks associated with remote shutdown procedures.
Strong Passwords and Authentication Methods
Strong passwords are the first line of defense against unauthorized access. Using a combination of uppercase and lowercase letters, numbers, and symbols creates a more complex and resistant password. Employing multi-factor authentication (MFA) adds another layer of security. This requires users to provide more than one form of verification, such as a code sent to their phone or an authenticator app.
These measures significantly reduce the risk of unauthorized access, even if a password is compromised. Regular password changes, using unique passwords for different accounts, and employing a password manager are also crucial steps.
Secure Network Configurations for Remote Access
Proper network configuration is essential for secure remote access. Firewall rules should be meticulously configured to restrict access to only authorized devices and users. Using a dedicated network segment or VLAN for remote access can further isolate remote connections from the internal network. Regularly updating firewall rules and software patches is paramount to address any emerging vulnerabilities.
Employing strong encryption protocols for network communication is vital to ensure the confidentiality and integrity of data transmitted during the shutdown process.
Use of VPNs for Secure Remote Shutdown
Virtual Private Networks (VPNs) provide a secure and encrypted connection over a public network. When remotely shutting down a computer, using a VPN is highly recommended. This is because it encrypts the communication between the remote user and the target computer, making it virtually impossible for eavesdroppers to intercept or modify the shutdown command. VPNs create a secure tunnel for the remote shutdown process, safeguarding sensitive data and preventing unauthorized access.
Employing a reputable VPN provider and regularly checking for updates and vulnerabilities are important.
Regular Security Audits
Regular security audits are essential for identifying and addressing potential vulnerabilities in the remote shutdown process. These audits should encompass network configurations, authentication mechanisms, and the overall security posture of the system. Audits should be conducted periodically, ideally on a monthly or quarterly basis, to ensure compliance with security policies and to proactively identify any emerging threats. The findings from these audits can be used to refine security protocols, address weaknesses, and enhance the overall security of the remote shutdown procedures.
Summary of Security Best Practices
| Practice | Description | Implementation | Importance |
|---|---|---|---|
| Strong Passwords and Authentication | Using complex passwords and multi-factor authentication | Employing a password manager, changing passwords regularly, and enabling MFA | Reduces the risk of unauthorized access |
| Secure Network Configurations | Restricting access to authorized devices and users | Configuring firewalls, using VLANs, and applying updates | Protects against unauthorized access attempts |
| Use of VPNs | Establishing an encrypted connection for remote access | Using a reputable VPN provider and maintaining updated software | Ensures confidentiality and integrity of remote shutdown commands |
| Regular Security Audits | Identifying and addressing potential vulnerabilities | Conducting periodic reviews of network configurations and security protocols | Proactively mitigates emerging threats and enhances security posture |
Troubleshooting Common Issues
Remote computer shutdown, while seemingly straightforward, can sometimes encounter unexpected hurdles. Understanding the common problems and their solutions is crucial for efficient and reliable remote administration. This section delves into troubleshooting steps for various issues, equipping you with the knowledge to diagnose and resolve them effectively.
Network Connectivity Problems
Network issues are frequently encountered when attempting remote shutdowns. These problems often stem from network configuration, firewall restrictions, or intermittent connectivity. Addressing these problems requires a methodical approach.
- Firewall Restrictions: Firewalls act as gatekeepers, potentially blocking the communication required for remote shutdown commands. Verify that the necessary ports are open and that the firewall rules permit the remote shutdown process. Check the firewall settings on both the client and server machines. For example, if using SSH, ensure port 22 is open on the server’s firewall.
- Network Configuration Errors: Incorrect network configurations, such as mismatched IP addresses or DNS issues, can disrupt communication. Double-check the IP address, subnet mask, and default gateway settings on both the client and server. Ensure the network protocols (e.g., TCP/IP) are properly configured. Consult the network documentation if needed.
- Intermittent Connectivity: Unstable or unreliable network connections can lead to failed remote shutdown attempts. If the connection drops or becomes unreliable, the shutdown command might be interrupted, resulting in incomplete or unsuccessful actions. Try using a more stable network connection, or investigate potential network congestion or interference. Consider troubleshooting network hardware, such as routers and switches.
Software-Related Issues
Software-based remote shutdown tools might encounter errors due to compatibility issues, configuration problems, or system conflicts.
- Software Compatibility Problems: The remote shutdown software might not be compatible with the operating system or other software installed on the target machine. Ensure the remote shutdown software is compatible with the operating system and any existing security software. Verify the system requirements listed by the software vendor.
- Configuration Errors: Incorrect configurations within the remote shutdown software can lead to failed attempts. Carefully review the software’s configuration settings, ensuring that the target machine’s IP address or hostname is correctly entered. Verify the credentials (username and password) are correct.
- System Conflicts: Conflicting processes or software running on the target machine can hinder the remote shutdown process. Check for any other programs or services that might be interfering with the remote shutdown tool. Temporarily disable or stop potentially conflicting applications to isolate the problem.
Troubleshooting Steps Summary
A structured approach to troubleshooting is essential. The following table summarizes common problems, their possible causes, troubleshooting steps, and preventive measures.
| Problem | Possible Cause | Troubleshooting Steps | Prevention |
|---|---|---|---|
| Failed Remote Shutdown | Network connectivity issues, firewall restrictions | Verify network connectivity, check firewall rules, ensure ports are open | Use a stable network connection, configure firewalls correctly |
| Error Message: “Connection Refused” | Incorrect IP address, network configuration error | Verify target machine’s IP address, check network settings, ensure correct ports are open | Verify IP addresses and network settings before initiating the shutdown |
| Error Message: “Command Failed” | Software compatibility issues, incorrect configuration | Check software compatibility, review software configuration, ensure target machine is accessible | Ensure software compatibility, double-check configurations |
Real-World Use Cases
Remote shutdown, while seemingly a simple task, offers a surprising array of practical applications in various professional and personal settings. From streamlining IT maintenance to ensuring secure data handling, the ability to remotely control a computer’s power cycle can significantly improve efficiency and security. This section explores real-world scenarios where remote shutdown proves invaluable.
IT Department Efficiency
Remote shutdown is a crucial tool for IT departments. Automated scripts can be scheduled to shut down machines at the end of the workday, saving energy and preventing accidental overnight use. This proactive management allows for scheduled maintenance tasks to be performed without interrupting user workflows. Moreover, it facilitates rapid response to security incidents, allowing immediate isolation of compromised systems.
Server Management and Maintenance
Maintaining servers often requires downtime for updates and repairs. Remote shutdown allows administrators to schedule and execute these tasks without the need for physical access or user intervention. This is particularly beneficial in geographically dispersed setups where travel is costly or time-consuming. Automated scripts can be configured to initiate shutdown procedures based on pre-defined schedules or events, ensuring that critical maintenance tasks are performed efficiently.
Data Security and Compliance
Remote shutdown plays a significant role in data security and regulatory compliance. In cases of suspected breaches or security incidents, administrators can swiftly isolate potentially compromised systems. This immediate action minimizes the potential impact of a security incident and ensures compliance with data security regulations. Furthermore, remote shutdown allows for secure decommissioning of equipment, safeguarding sensitive data from unauthorized access.
Case Study: Remote Shutdown for a Retail Store
A retail store with multiple locations uses remote shutdown to manage their point-of-sale (POS) systems. At the end of each business day, a scheduled script automatically shuts down all POS terminals. This process conserves energy, reduces the risk of accidental data loss, and streamlines the end-of-day closing procedures. Furthermore, the ability to remotely shut down specific POS terminals in case of a security incident ensures that only the affected terminals are isolated.
This significantly reduces the potential for data breaches and enhances security protocols. This proactive approach to maintenance and security reduces the likelihood of operational disruptions and ensures data integrity, supporting the store’s overall operational efficiency and security posture. This remote shutdown process also helps the store comply with industry regulations and internal security policies.
Impact on Efficiency
Remote shutdown significantly improves efficiency across various departments. By automating shutdown procedures, IT administrators can focus on more strategic tasks, leading to reduced operational costs and enhanced productivity. The ability to perform maintenance tasks remotely eliminates the need for physical presence, saving time and resources. Moreover, rapid response to security incidents minimizes downtime and data loss, maintaining business continuity.
Final Conclusion
In conclusion, remotely shutting down a computer offers significant advantages in terms of efficiency and convenience, particularly in distributed work environments. By understanding the diverse methods, software, and security protocols, you can confidently implement remote shutdown solutions that meet your specific needs. This guide equips you with the knowledge and tools to navigate the intricacies of remote shutdown, enabling you to effectively manage your computer systems from anywhere.


Leave a Reply